Setting up Dovecot and Roundcube with Azure Active Directory B2C
This post explains how to configure Roundcube that connects to Dovecot to fetch mails letting the user authenticate against an Azure Active Directory B2C.
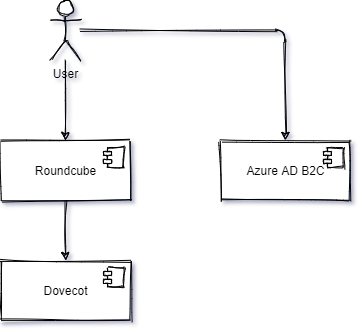
Azure AD
In Azure AD B2C we need to:
- Register an App for Roundcube
- Register an App for Dovecot
- Create a User Flow to log Users into Roundcube
- Create a resource owner password credential (ROPC) flow to log Users into Dovecot whit PLAIN
App registrations
First of all let's register a new app in AAD App registrations for Roundcube: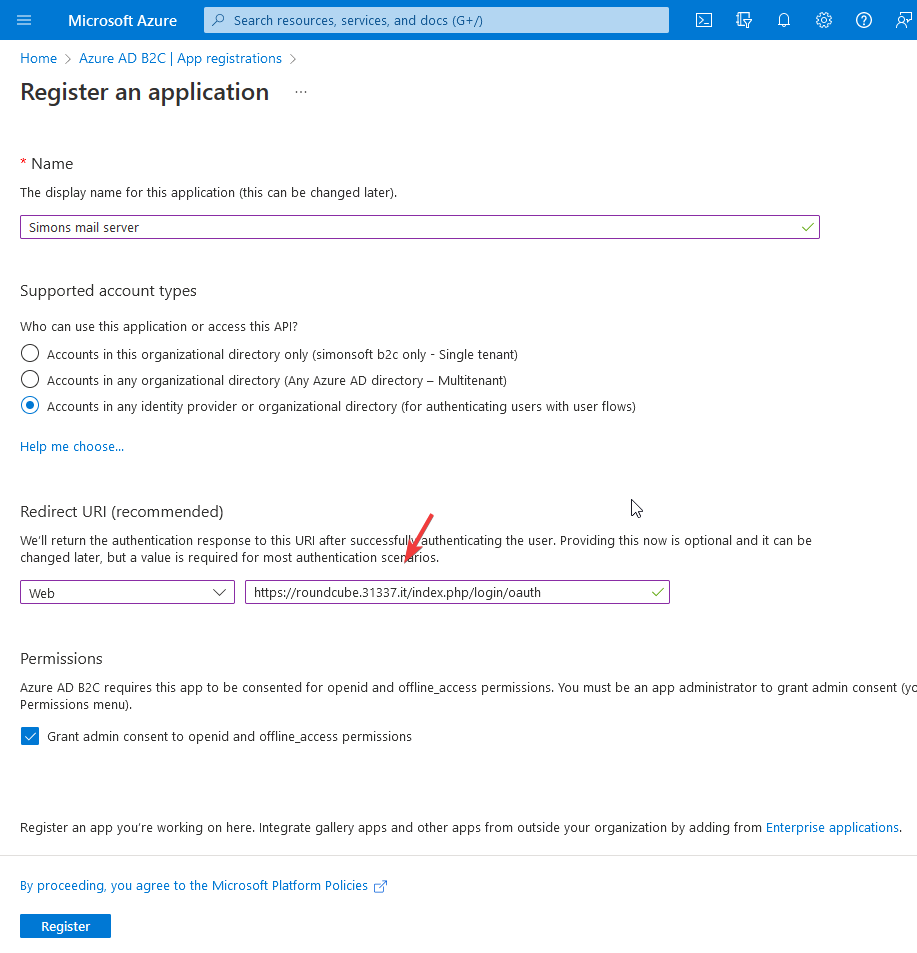
Change the domain of the redirect uri to the domain of your Roundcube installation.
Now let's create an OAuth client secret for Roundcube. Go to Certificates and secrets for the App we just registered, and create a new secret.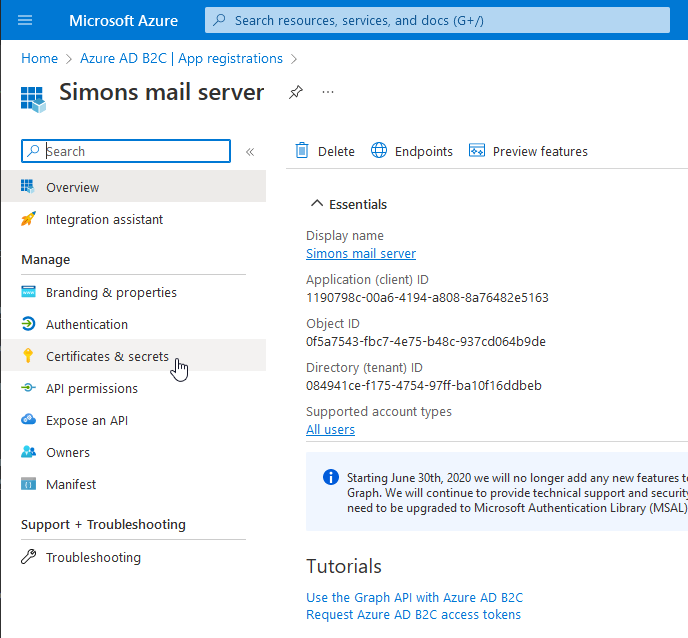
Save this secret for later, we will need it when configuring Roundcube.
Do the same for Dovecot, but for the Dovecot app, under Advanced settings -> Enable the following mobile and desktop flows, select Yes to treat the application as a public client.

Also, for the Dovecot app, we need to set "oauth2AllowImplicitFlow": true in the App Manifest.
This setting is required for the ROPC flow we will create in the next chapter.
Sign in/up and ROPC flow
Now let's configure the Sign in/up flow, so users can log in to Roundcube. But first we need to add a custom attribute for our users, that will hold the Dovecot username for login.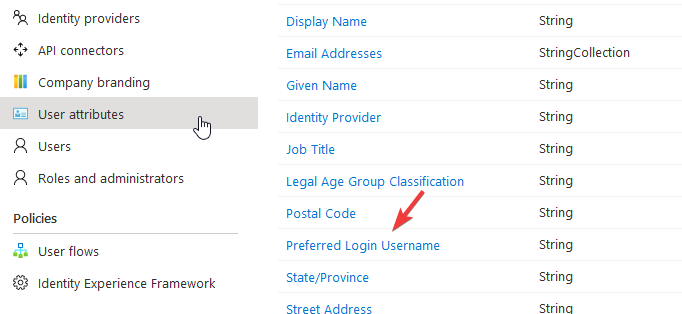
How to populate this user attribute is left as exercise for the reader (use API connectors).
And now create a new flow. Call it something you like (mine is called B2C_1_SignUpIn), and add the attribute as claim for Roundcube: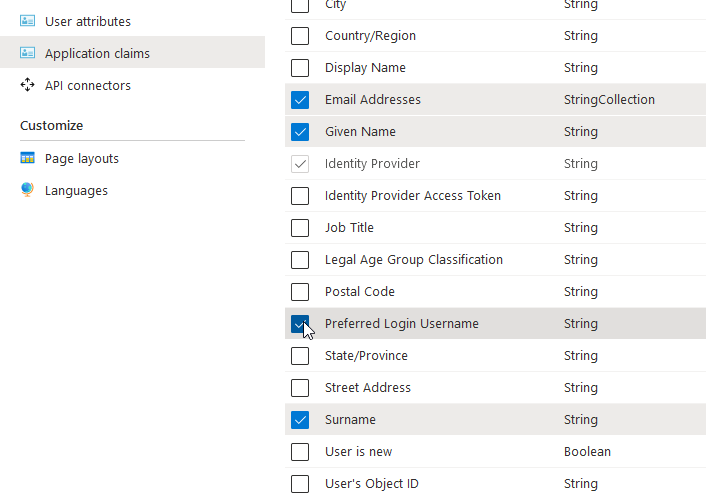
This flow is used by Roundcube to log users in.
We need one more, to allow Dovecot to log users in with username and password for plain auth, but authenticating them against our B2C AD. To do that, we need to create a resource owner password credential flow.
Once created, add the custom user attribute to the application claims like for the flow created previously.
We are done here. Next up is Roundcube.
Roundcube
Download and install it (at the time of writing the actual version is 1.6.0, and I tested everything with this version), and following this wiki page, we can configure OAuth.
We just have to add some parameters in roundcube/config/config.inc.php:
1 | // ---------------------------------- |
That's it for Roundcube.
Dovecot
Dovecot docs are here. We need to configure conf.d/10-auth.conf like this:
1 | auth_mechanisms = plain oauthbearer xoauth2 |
/etc/dovecot/dovecot-oauth2.conf.ext looks like this:
1 | tokeninfo_url = https://<yourB2Cdomain>.b2clogin.com/<yourB2Cdomain>.onmicrosoft.com/b2c_1_signupin/oauth2/v2.0/token?token= |
and /etc/dovecot/dovecot-oauth2.plain.conf.ext looks like this:
1 | grant_url = https://<yourB2Cdomain>.b2clogin.com/<yourB2Cdomain>.onmicrosoft.com/b2c_1_ropc_auth/oauth2/v2.0/token?scope=<Dovecot app registration client id> |
Now we need to populate /etc/dovecot/keys/ with the keys from our OAuth provider (AAD). Go to https://<yourB2Cdomain>.b2clogin.com/<yourB2Cdomain>.onmicrosoft.com/b2c_1_signupin/discovery/v2.0/keys, and copy the keys key. It's something like this:
1 | {"kid":"X5eXk4xyo...aNk","nbf":1493763266,"use":"sig","kty":"RSA","e":"AQAB","n":"tVKUtcx_...Xw"} |
Create a file /etc/dovecot/keys/<App registration client id>/RS256/<kid> and put the key you copied above in that file.
The end
Restart Apache/Nginx, restard Dovecot, and try to log in. Everything should work.
Nice.
Bye.